Earlier this year, we shared information on upcoming requirements for using PayPal APIs.
In this post, I’ll update the status of those changes for PayPal and for other gateways and introduce a plugin we’ve developed to help site owners navigate through the required changes.
What’s happening?
All payment gateways, including PayPal, Stripe, Braintree, and Authorize.net (and really any service that uses an API) are updating their API servers to only accept requests made using the new TLS 1.2 protocol for encryption.
What do I need to do?
Ask your web host or server admin to make sure your server supports TLS 1.2. Specifically your web server should:
- Run OpenSSL 1.0.1 or higher, or another cryptographic library that supports TLS 1.2
- Run PHP version 5.5.19 or higher.
- Run cURL version 7.34.0 or higher.
What if I can’t upgrade my server?
The optimal fix for this issue is to upgrade your server software, and you must be running OpenSSL 1.0.1+ or the latest version of an alternative cryptographic library. The TLS 1.2 protocol is defined within the cryptographic library.
There are other reasons to upgrade PHP and cURL, including security reasons, but with respect to TLS 1.2, the versions recommended above mostly just tell the software to use the TLS 1.2 protocol. You may be able to get a lower version of PHP and cURL to use TLS 1.2 by adding the following code to your active theme’s functions.php or a custom plugin. Note that if the TLS 1.2 protocol becomes compromised in the future, you’ll need to adjust this code to force whatever new protocol takes its place.
That’s pretty complicated?
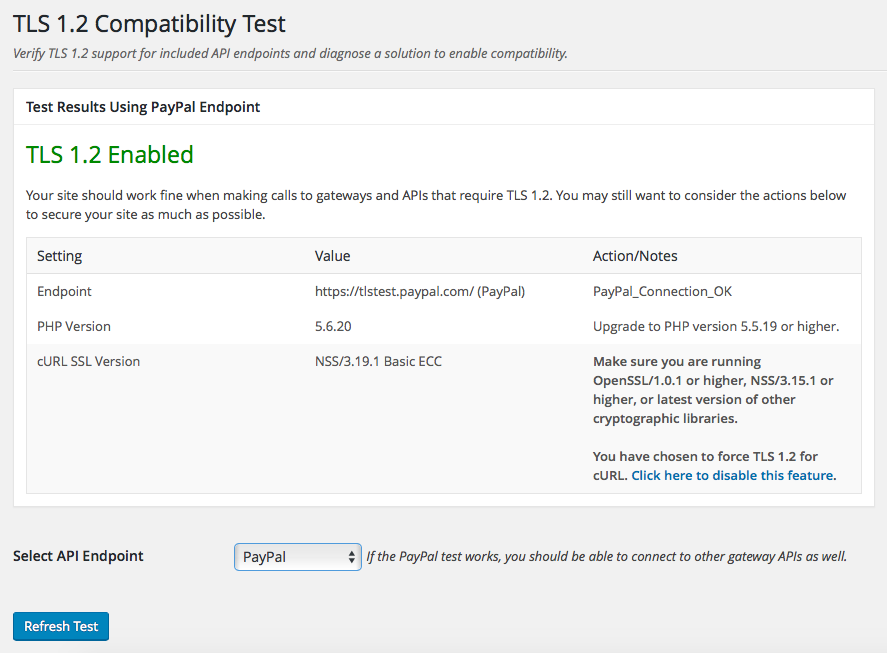
I’m trying to write this all out as clear as possible, but it is confusing. To help with things we’ve developed a plugin to help diagnose if TLS 1.2 is enabled on your site and what steps to take, including an option to force TLS 1.2 in cURL similar to the code gist above.
Get the TLS 1.2 Compatibility Test Plugin from the WordPress.org
When do I need to make these changes?
Ideally, you should make these changes as soon as possible to make sure your site is as secure as possible. Other than that, the main driver behind this change is the PCI Security Standards Council and they have set a deadline of June 30th, 2018, after which time you would risk losing PCI Compatibility status. This is an extension of the previous deadline of June 30th, 2016.
Your payment gateway will likely require the change sooner. PayPal was going to force TLS 1.2 today (June 17th, 2016), but has since extended their own deadline to June 30th 2017.
Other gateways were set to start requiring TLS 1.2 after June 30th, 2016 and may or may have extended that deadline because of the PCI SSC extension. You should check with your gateway to get the exact date… or just upgrade ASAP.
What might go wrong?
Whenever you upgrade your server, especially PHP, things might break. So it’s important to do these updates under the guidance of a trained sysop or with your host. Make any and all backups you can of your server, your files, and your database before starting the upgrade.
WordPress and most popular plugins, like Paid Memberships Pro, will work with newer versions of PHP. However some custom code of yours might rely on earlier PHP versions. I’m hesitant to say this, but generally you can upgrade PHP, then test things to see if anything broke, and then fix any code that is no longer working properly. Or you can consult with the developer who built the custom code and ask them if they expect any problems running the code under the newer version of PHP.
When upgrading PHP, you may also need to upgrade or reinstall some “PHP modules” that are used by your site. These might include the cURL library itself, the Multibyte String library, or others.
Some third party APIs outside the major gateways and name brand web companies may not have updates the web servers their APIs are running on to support TLS 1.2. If you upgrade your server to use TLS 1.2 and specifically if you use the gist above or our compatibility plugin to force TLS 1.2, API requests to these servers may fail. In these cases, you really should ask the entity managing the API to upgrade their servers to support the latest security protocols.
Why are these changes necessary?
When computers talk with each other and they want to keep the communication secret, encryption is used. In practice this means that visitors to the HTTPS version of your site use encryption so information like credit card numbers and billing addresses are kept secret when being entered into a form.
To make all of this work, standard “encryption protocols” are used so web browsers and web servers can communicate in a secure way. Previously, the SSL protocol was the standard, which is why you likely purchased something called an “SSL certificate” for your site. Third party SSL certificates authenticate that you are the true owner of your domain so browsers can confidently engage in SSL encrypted communication with the web server.
Encryption is also used when software like Paid Memberships Pro communicates with payment gateways like PayPal through its APIs. The same encryption protocols used when you visit a website in your browser are used when your web server makes a request to an API. Again, the SSL protocol was most popular for this.
However, several vulnerabilities have been found with SSL (most notably the Heartbleed and POODLE attacks) and a new protocol has been adopted called TLS (Transport Layer Security). This requires a number of updates to both browsers and web servers.
- Upgrades to servers to use TLS 1.2 when connecting to outside APIs (the topic of this post)
- Upgrades to API servers to use TLS 1.2 (what the gateways are doing)
- Upgrades to web browsers to use TLS 1.2 when connecting over HTTPS
- Upgrades to SSL/TLS certificates and web servers to use TLS 1.2 to serve sites over HTTPS
In Summary
Use the TLS 1.2 Compatibility Test plugin to diagnose if your site is already using TLS 1.2 and to get recommendations for how to upgrade your server to enable TLS 1.2.
While the PCI SSC and gateways have decided to extend the deadline for migrating to exclusive TLS 1.2 usage, you really should make this change as soon as possible to make sure your site is secure.
I’ve tried my best to make this post as clear as possible, but this is a technical issue. Let me know if there is something we can do to be more clear or helpful. If in doubt, forward this post to your host or web master to work through on your site.

